Nmap is one of the widely used and most popular tools among cybersecurity professionals, security researchers, hackers & network engineers, and learners as well. It is an open-source licensed tool mainly used for performing discovery such as ports, operating systems, etc., and auditing or determining security over the network.
Nmap is a command-line utility that comes pre-installed with Kali Linux. You can also download it for other operating systems from below link.
Nmap: Network Scanning Tool
Download Nmap, the powerful network scanning tool used for network discovery and security auditing. It is widely used by administrators, network engineers, and security professionals to map and secure networks.
Nmap also has an official graphical user interface version known as Zenmap. However, in this video, we will look at the command line version i.e. Nmap. Zenmap can also, be used similarly.
Nmap has a scripting engine known as Nmap Scripting Engine – NSE which is a powerful extension for Nmap which allows various scripts to connect with Nmap & extend its scope and potential to the next level.
Nmap has several other components such as a flexible data transfer, redirection, and debugging tool (Ncat), a utility for comparing scan results (Ndiff), and a packet generation and response analysis tool (Nping).
Table of Contents
- Why Nmap is a preferred choice?
- Nmap First Look
- Basic of Port Scanning
- Various Port & Flag Based Scanning with Nmap
- 1. TCP SYN Scan
- 2. TCP Connect Scan
- 3. UDP Scan
- 4. SCTP INIT Scan
- 5. XMAS SCAN
- Performing Xmas Scan
- 6. TCP Maimon Scan
- 7. TCP Custom Flag Scan
- Version & Service Detection with Nmap
- OS Detection with Nmap
- Nmap Scripting Engine (NSE)
Why Nmap is a preferred choice?
- Flexible: Supports dozens of advanced techniques for mapping out networks filled with IP filters, firewalls, routers, and other obstacles. This includes many port scanning mechanisms (both TCP & UDP), OS detection, version detection, ping sweeps, and more.
- Powerful: Nmap has been used to scan huge networks of literally hundreds of thousands of machines: Portable: Most operating systems are supported, including Linux, Microsoft Windows, FreeBSD OpenBSD, Solaris, IRIX, Mac OS X, HP-UX, NetBSD, Sun OS. Amiga, and more.
- Easy: While Nmap offers a rich set of advanced features for power users, you can start as simply as “nmap –v –A targethost”. Both the traditional command line and graphical (GUI) versions are available to suit your preference. Binaries are available for those who do not wish to compile Nmap from the source.
- Free: The primary goals of the Nmap Project are to help make the Internet a little more secure and to provide administrators/auditors/hackers with an advanced tool for exploring their networks. Nmap is available for free download and also comes with full source code that you may modify and redistribute under the terms of the license.
- Well Documented: Significant effort has been put into comprehensive and up-to-date man pages, whitepapers, tutorials, and even a whole book! Find them in multiple languages here.
- Supported: While Nmap comes with no warranty, it is well supported by a vibrant community of developers and users. Most of this interaction occurs on the Nmap mailing lists. Most bug reports and questions should be sent to the map-dev list, but only after you read the guidelines. We recommend that all users subscribe to the low-traffic Nmap hackers announcement list. You can also find Nmap on Facebook and Twitter. For real-time chat, join the #nmap channel on Freenode or EFNet.
- Acclaimed: Nmap has won numerous awards, including "Information Security Product of the Year" by Linux Journal, Info World, and Codetalker Digest. It has been featured in hundreds of magazine articles, several movies, dozens of books, and one comic book series. Visit the press page for further details.
- Popular: Thousands of people download Nmap every day, and it is included with many operating systems (Redhat Linux, Debian Linux, Gentoo, FreeBSD. OpenBSD, etc). It is among the top ten (out of 30,000) programs at the Freshmeat Net repository. This is important because it lends Nmap its vibrant development and user support communities.
Nmap First Look
a. Boot Kali Linux & Start the Terminal:
b. Type the following command to start Nmap:
c. When you start Nmap with no additional parameters, it will display the options screen (for a complete list of options).
d. There are a lot of options in Nmap and a detailed list can be seen on the manual page.
e. The general syntax for using Nmap, as shown in the above output, is -
f. For example, we will take an illustration of how Nmap works with a simple example as shown in the above output.
g. Output for the above example will look like the following:-
Basic of Port Scanning
Nmap is one of the efficient port scanners and by default scans the first 1000 IP ports the target is when you use the Nmap <target> command directly without conceiving any port or port range, it will scan the first 1000 TCP ports.
Nmap provides ports in six states, which are:
- Open: An application is actively accepting TCP connections, UDP datagrams, or SCTP associations on this port. Finding these is often the primary goal of port scanning. Security-minded people know that each open port is an avenue for attack.
- Closed: A closed port is accessible (it receives and responds to Nmap probe packets), but there is no application listening on it. They can help show that a host is up on an IP address (host discovery, or ping scanning), and as part of Os detection.
- Filtered: Nmap cannot determine whether the port is open because packet filtering prevents its probes from reaching the port. The filtering could be from a dedicated firewall device, router rules, or host-based firewall software.
- Unfiltered: The unfiltered state means that the port is accessible, but Nmap is unable to determine whether it is open or closed. Only the ACK scan, which is used to map firewall rulesets, classifies ports into this state.
- Open | Filtered: Nmap places ports in this state when it is unable to determine whether a port is open or filtered. This occurs for scan types in which open ports give no response. The lack of response could also mean that a packet filter dropped the probe or any response it elicited.
- Closed | Filtered: This state is used when Nmap is unable to determine whether a port is closed or filtered. It is only used for the IP ID idle scan.
Various Port & Flag Based Scanning with Nmap
Important points:
a. To specify port range use the following optional parameter:
b. To select all ports use the following optional parameter:
c. To perform a fast scan with limited ports use the following optional parameter:
d. To see the backend processing information use the following optional parameter:
1. TCP SYN Scan
TCP SYN Scan is also referred to as a Half-Open Scan. It is a quick, default & most popular scan and has the ability to scan thousands of ports within seconds (considering fair internet connection not restricted by firewalls). It never completes the whole 3-way handshake and provides clear results between open, closed, and filtered ports.
Flag for SYN Scan: -sS
Performing TCP SYN Scan
a. Boot Kali Linux & Open Terminal
b. Use the following command for TCP SYN Scan & check the below output.
2. TCP Connect Scan
TCP Connect scan detects open ports by completing the 3-way handshake process (establishes the full connection) and breaks down connecting by sending the RST packet to the target. If SYN Scan is not used, this is the default scan and doesn't require any superuser privileges.
In this scan, we send a syn packet to the target on specified port numbers depending upon the port's state the following can happen:
a. If the port is open, we receive an SYN + ACK packet back along with the required data. After this, we send the ACK packet and kill the connection by sending RST Packet.
b. If the port is closed, we receive an RST packet in response.
Flag for SYN Scan: -sT
Synax: nmap -sT <target> <other optional parameters>
Performing TCP SYN Scan
a. Boot Kali Linux & Open Terminal.
b. Use the following command for TCP Connect Scan & check the below output.
3. UDP Scan
There are some services and protocols which operate on UDP such as DNS & DHCP, UDP Scan works by sending UDP Packets to every specified port on the target system. It can work in combination with TCP Scans such as SYN Scan to check both protocols in the same scan.
It is usually slower and complex compared to TCP Scans due to which it is usually ignored by pentesters.
Flag for UDP Scan: -sU
Syntax: nmap -sU <target> <other optional parameters>
Performing UDP Scan
a. Boot Kali Linux & Open Terminal.
b. Use the following command for UDP Scan & check the below output –
4. SCTP INIT Scan
SCTP is a relatively new alternative to the TCP and UDP protocols, combining most characteristics of both and also adding new features like multi-homing and multi-streaming It is mostly being used for SS7/SIGTRAN-related services but has the potential to be used for other applications as well SCTP INIT scan is the SCTP equivalent of a TCP SYN scan. It can be performed quickly, scanning thousands of ports per second on a fast network not hampered by restrictive firewalls Like SYN scan, INIT scan is relatively unobtrusive and stealthy since it never completes SCTP associations. It also allows clear reliable differentiation between the open-closed, and filtered sites (source - nmap.org).Flag for SCTP INIT Scan: -sY
Syntax:
nmap -s <target> <other
optional parameters>
Performing SCTP INIT Scan
a. Boot Kali Linux & Open Terminal.b. Use the following command for SCTP INIT Scan & check the below output –
5. XMAS SCAN
Xmas scan is a type of scan that exploits a loophole present in TCP RFC to put a fine line between open and closed ports. It will not work against any latest version of the Windows operating system and will work for OSes having TCP’s RFC-793 implementation. In this scan, we send a TCP Frame to a remote device with FIN, Push & URG flag set Along with XMAS Scan, we will also look at Null & Fin Scan which works by it.
In NULL Scan, the TCP flag header is set to 0
In FIN Scan, Only FIN bit is set in the TCP flag header
In Xmas Scan, FIN, PSH & URG bits are set in the TCP flag header
Flag for Null Scan: - sN
Flag for Fin Scan: - sF
Flag for Xmas Scan: - sX
Syntax: nmap -sX/N/F <target> <other optional parameters>
Performing Xmas Scan
a. Boot Kali Linux & Open Terminal.
b. Use the following command for Xmas Scan & check the below output –
6. TCP Maimon Scan
The Maimon scan is named after its discoverer, Uriel Maimon. He described the technique in Phrack Magazine issue #49 (November 1996). Nmap, which included this technique, was released two issues later. This technique is the same as NULL, FIN, and Xmas scans, except that the probe is FIN/ACK. According to RFC 793 (TCP), an RST packet should be generated in response to such a probe whether the port is open or closed. However, Uriel noticed that many BSD-derived systems simply drop the packet if the port is open.
Flag for Xmas Scan: -sM
Syntax: nmap -sM <target> <other optional parameters>
It can be performed similarly as per the above scans.
7. TCP Custom Flag Scan
This functionality of Nmap allows you to design a TCP scan by specifying TCP Flags according to your requirement
- -- scanflags argument is used to specify Custom TCP Scan.
To use this scan, just combine the symbolic numeric identifiers of each flag and perform the scan.
Syntax: nmap --scan flags <flag combination> <target> <other optional parameters>
- Ex: nmap ---scan flags SYNURGEIN scanme.nmap.org .
This will choose scan based on SYN, URG & FIN Flags. This scan can be performed similarly as per the above scans.
Version & Service Detection with Nmap
Nmap is most popular among other port scanners, it has pre-built functionality which allows you to detect the services running on specific ports & their versions. It can be carried out using Version & Service Scan option in Nmap which an optional parameter.
Flag for Service & Version Scan: -sV
Syntax: nmap -sV <target><other optional parameters>
Performing Service & Version Scan
a. Boot Kali Linux & Open Terminal output.
b. Use the following command for Service & Version Scan & check below.
OS Detection with Nmap
Operating System detection is one of the best features of Nmap, which allows detecting the target's OS by looking into the TCP/IP stack implemented on the target. Each Operating System varies in TCP/IP Stack implementations allow gathering the information about the operating system just by crawling into stack implementation and looking for differences.
Flag for OS Detection: -sO
Flag for Guessing OS Detection: --osscan-guess; --fuzzy
Syntax: nmap -sO <target> <other optional parameters>Performing OS Detection
a. Boot Kali Linux & Open Terminal.
b. Use the following command for OS Detection & check the below output:
c . In the above example, the Nmap fails to exactly determine the operating system so it runs Aggressive OS Guesses and you can see the results based on accuracy in percentage in the above output.
Nmap Scripting Engine (NSE)
Nmap Scripting Engine (NSE) is one of the most powerful and advanced features of Nmap. It allows us to write simple scripts or use existing scripts for specific Jobs using Nmap.
- These scripts are written in the LUA Programming Language.
- According to nmap.org, NSE is designed with the following in mind.
Network Discovery
This is Nmap's bread and butter. Examples include looking up whois data based on the target domain, querying ARIN, RIPE, or APNIC for the target IP to determine ownership performing ident lookups on open ports, SNMP queries, and listing available NFS/SMB/RPC shares and services.
More Sophisticated Version Detection
The Nmap version detection system can recognize thousands of different Services through its probe and regular expression signature-based matching system, but it cannot recognize everything.
Vulnerability Detection
When a new vulnerability is discovered, you often want to scan your networks quickly to identify vulnerable systems before the bad guys do. While Nmap isn't a comprehensive vulnerability scanner. NSE is powerful enough to handle even demanding vulnerability checks. When the Heartbleed bugs affected hundreds of thousands of systems worldwide. Map developers responded with the SSL-heartbleed detection script within 2 days.
Backdoor Detection
Many attackers and some automated worms leave backdoors to enable later re-entry. Some of these can be detected by Nmap’s regular expression-based version detection, but more complex worms and backdoors require NSE's advanced capabilities to reliably detect.
Vulnerability Exploitation
As a general scripting language, NSE can even be used to exploit vulnerabilities rather than just find them. The capability to add custom exploit scripts may be valuable for some people (particularly penetration testers), though we aren't planning to turn Nmap into an exploitation framework such as Metasploit.
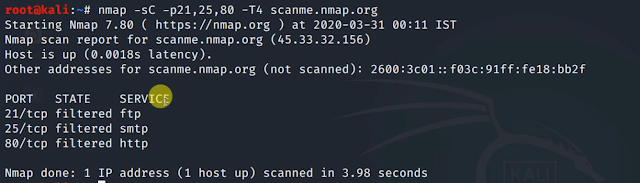
Flag for NSE: -sC; --Script (for custom scripts)
Syntax: nmap -s <target> <other optional parameters >
Or
nmap -script <script> <target> <optional parameters>
Using Nmap Scripting Engine
a. Boot Kali Linux & Start Terminal
b. Refer to the below example & Sample output for the working of NSE -