Table of Contents
In this article, we are going to tackle an easy box from VulnHub. If you’re not familiar with VulnHub, then read my Articles.
- Learn More:
Vulhub: Vulnerable by Design
This resource explores Vulhub, a platform designed to provide vulnerable environments for practicing and learning various cybersecurity concepts such as penetration testing, ethical hacking, and exploit development. Vulhub offers a range of intentionally vulnerable virtual machines that allow security enthusiasts to hone their skills in a safe and controlled environment.
Settings up
Before getting started, You need an isolated network environment on VirtualBox. The box, we are going to write up is called Jangow01-1.0.1.
1. Download the OVA mirror file from VulnHub.
Jangow: 1.0.1
This is a vulnerable virtual machine designed for penetration testing and learning purposes. Jangow provides a hands-on opportunity to practice web application security testing and hone your skills in identifying and exploiting vulnerabilities. By exploring this VM, users can gain practical experience in web application security.
2. The settings up are quite easy and it is similar to the past.
- Open VirtualBox.
- Click on import, and browse the file from the Download directory.
3. Check the Network Adapter, and if it is set to a Host-only adapter or not.
Once you are done with the settings, let’s start the instance VMs.
The instance is ready, and we are going for the enumeration phase.
Enumeration
Now, switch to Kali Linux. Next, we are going to identify the IP address with the help of netdiscover. Open a terminal and type the following command:
We have discovered the target IP address
i.e., “192.168.56.118”.
Let's Perform a network scan to detect what
ports are open, which is already known as an essential part of the enumeration
process. This offers us the opportunity to better understand the attacking
surface, and design targeted attacks. As in most cases, we are going to use the
famous Nmap tool.
Network Scanning using Nmap
- -sC: Perform a script scan using the default set of scripts.
- -sV: Enables version detection, which will detect what versions are running on what port.
From the output, we have spotted that we
have ports 21, and port 80 open.
- Port 21/TCP runs an FTP service, which means, that if you have a valid credential then it will be easy to gain login access to the server.
- Port 80/TCP running an HTTP service, which indicates that there is some vulnerable website being hosted.
To look at the contents ourselves, we can
open a web browser of our choice and navigate to the target's IP address in the
URL bar at the top of the window. The URL redirects us to a broken link page:
We found that directory listing is enabled
on the target machine. We found one folder named ‘site/’ in the current
directory.
Foothold
Following the previously shown link brought us to this “Grayscale” site. Looking around, there doesn’t seem to be anything too interesting except for the “Buscar” page found in the top right.
That’s interesting, it looks like it’s performing some kind of post request. It seems like, this website is vulnerable to Local File Inclusion.
Local File Inclusion Vulnerability
It means we can search for anything from here. Let's see what can we do, with this LFI vulnerability.
Let’s search for the ls command to list the files and directories. Switch to view page source mode by clicking right on the mouse > click on View Page source.
For a better view, switch to view page source by right click on the mouse.
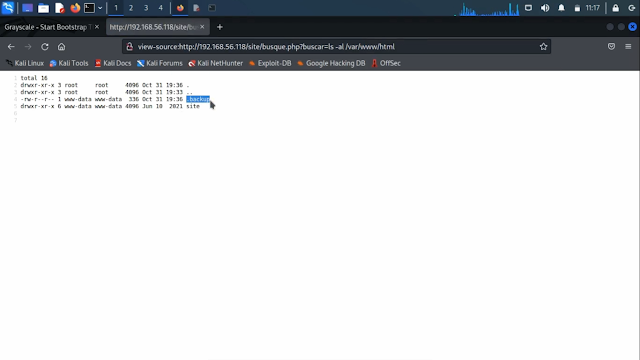
Let me search again the ls -al command to list all hidden files.
From the output, we have spotted a WordPress directory existing within it. After visiting the WordPress page, we noticed that this WordPress is in a broken state. This may be happening, because WordPress may not be able to access the database, or maybe the WordPress database may be deleted.
Let's switch back to the buscar tab, and find out if any other files may exist or not, which may help us to gain an FTP connection.
I quickly noticed that there’s a “config.php” file that seems to contain something else. Open the file using the cat command and read the contents within it.
This may contain a username and password which may help us to gain access with the FTP client tool.
Attempting Login Session Retrieval with FTP Client Tool
Let’s try to attempt login access using the FTP client tool using the passwords with the username, but I quickly discovered that this does not work.
.png)
I noticed that there’s a “.backup” file that seems to contain backup database credentials. Read the file using the cat command.
Let’s again try to attempt to gain access to the server using the FTP client tool.
You can find out the user flag from the jangow01 directory. You can read the flag.txt file by downloading it from the FTP server using the get command.
Exploitation: Way to Find a Reverseshell Connection
We need to find a way to escalate our privileges from the user jangow01 to the super admin role. One way to try this is by checking if a reverse shell connection is possible or not. Let's examine the possible methods one by one.Method 1: Using php-reverse-shell.php
A reverse shell connection is possible if we push a php-reverse-shell file to the server and execute it.
We can chain this with the LFI vulnerability that we have already identified, in order to upload malicious PHP code to the target system that will be responsible for returning a reverse shell to us. We will then access this PHP file through the LFI and the webserver will execute the PHP code.
We can either create our own PHP code or use one of the many available php-reverse-shell that can be found online through a Google search.
Firstly, we have to create a “test.php” file using the nano text editor.
Paste the code by pressing ctrl+shift+v. Now,
modify the code so it can suit our needs. We are going to change the Listening
Host IP, and the Listening port variables to match our settings, and then we
will attempt to upload the file.
But the upload isn’t possible, as the jangow01 user doesn’t have any permission to modify the web directories.
Method 2: Using Netcat
A
reverse shell connection
can also be possible
with the Netcat command.
Type the following command:
This is also not possible in terms of reverse shell connection.
Method 3: Using the Bash Shell script
There is a method that can give us a reverse-shell connection . You find this code by searching on Google.
Modify this code IP address and port.
Take a look closer at the top of the URL bar at the top of the window, when we execute the script it automatically translates the bash script to a string.
There is a way to encode the bash script to an encoded URL string. Visit the URL encoder by searching on Google.
- Visit:
URL Encoder
URL Encoder is a simple online tool for encoding URLs. It converts special characters into a format that can be transmitted over the internet. This tool is useful for encoding URLs to ensure compatibility with various systems and for security purposes.
Load the output code to the buscar. Before running this script, you have to create a NetCat listener .
Once this command is run our terminal will appear stuck, however, our Netcat listener has caught a connection.
We got the foothold. The received shell is not fully interactive, however, we can make it a bit better by using Python3.
Finally, we have the fully interactive shell now. Switch the user to jangow01 using the sudo su command and paste the password.
Privilege Escalation
The next step is escalating to the root user in order to gain the highest privileges on the system. Switch to back the user jangow01 directory and list out all hidden files and directories that we have not listed before.
For Privilege Escalation, we are going to use a tool called LinPEAS, which can automate a big part of the enumeration process in the target system.
Privilege Escalation Enumeration with LinPEAS
- Download LinPEAS From Here:
PEASS-ng Releases
PEASS-ng is a collection of Windows-based tools for privilege escalation, allowing security professionals to assess and improve the security of Windows environments. This link leads to the releases page on GitHub, where you can find and download the latest versions of PEASS-ng tools.
Now, we have to transfer the LinPEAS.sh, file to our target system by using the FTP service.
On the target machine, you can verify by listing the files and directories.
As you can see, this file contains only read and write permission but does not have any execution permission.
After analyzing the output, we found a piece of important information that our target is vulnerable to these exploits.
Local Privilege Escalation Vulnerability in Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27)
Let’s try to exploit the get_rekt . You can find out the script from the exploit DB database.
- Click here to download:
Exploit Database: WordPress Plugin Insert or Embed Articulate Content into WordPress - Remote Code Execution
This exploit entry describes a vulnerability in the WordPress plugin "Insert or Embed Articulate Content into WordPress" that allows for remote code execution. Understanding and mitigating such vulnerabilities is essential for securing WordPress websites.
Upload this file to the server using the FTP service.
Compile the program to compile the exploit using the GCC command-line utility.
On execution, it creates a new file in the current directory. Now execute the output file. On successful execution, we can see that the kernel exploit grants us root.
You can find the root flag to complete the challenge.
Congratulations on the completion of capturing both flags.


.png)
.png)
.png)
.png)
.png)
.png)


.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)



